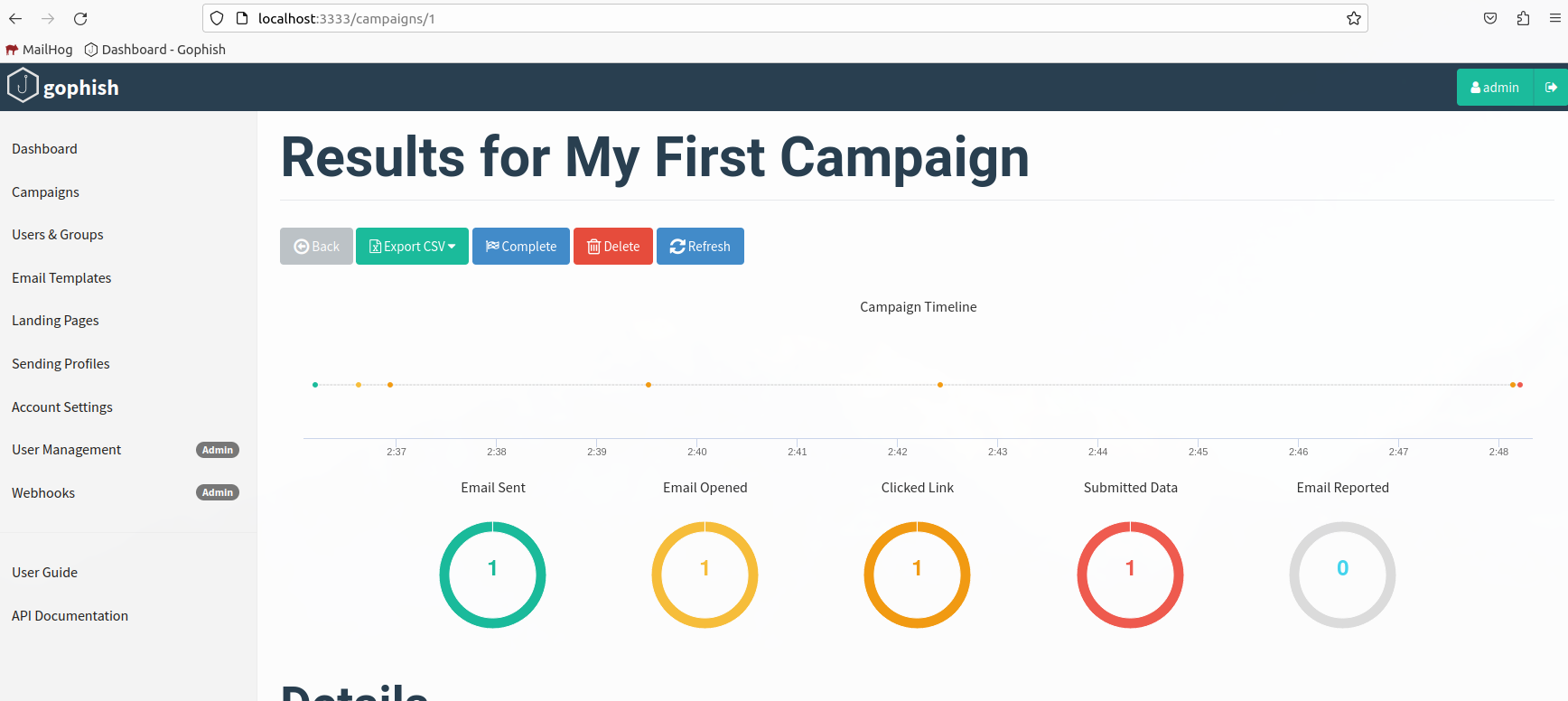
Basic Credential Harvesting
Create a new landing page.
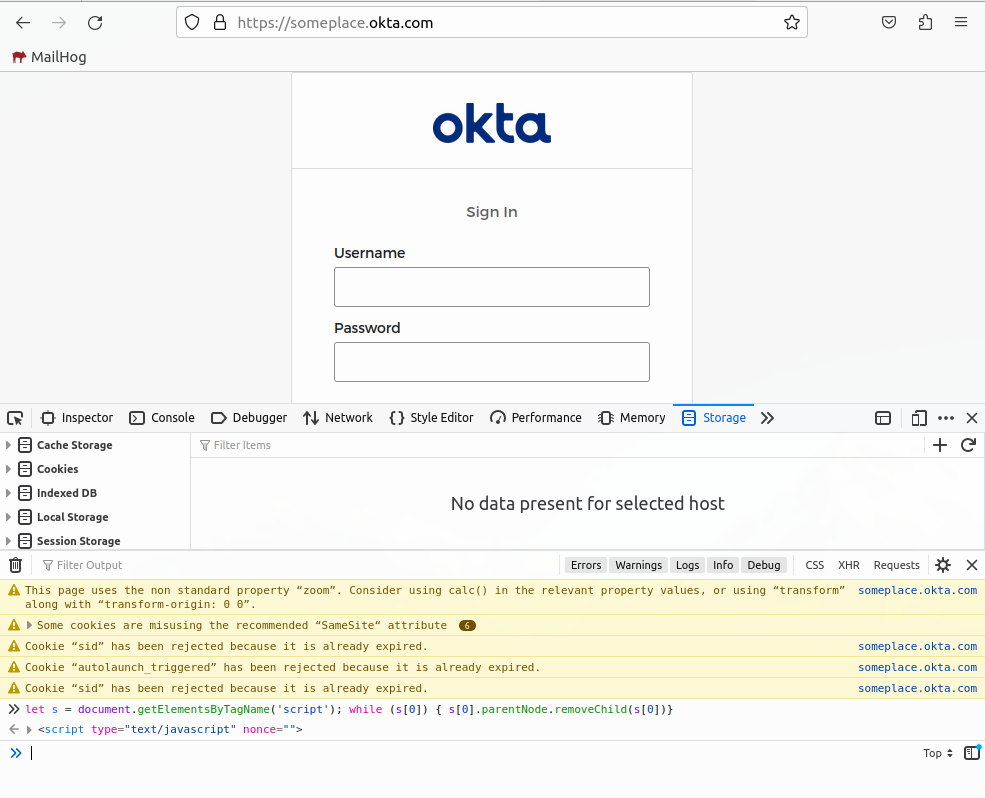
- open https://someplace.okta.com/
- open dev console (f12)
- in console run:
let s = document.getElementsByTagName('script'); while (s[0]) { s[0].parentNode.removeChild(s[0])}
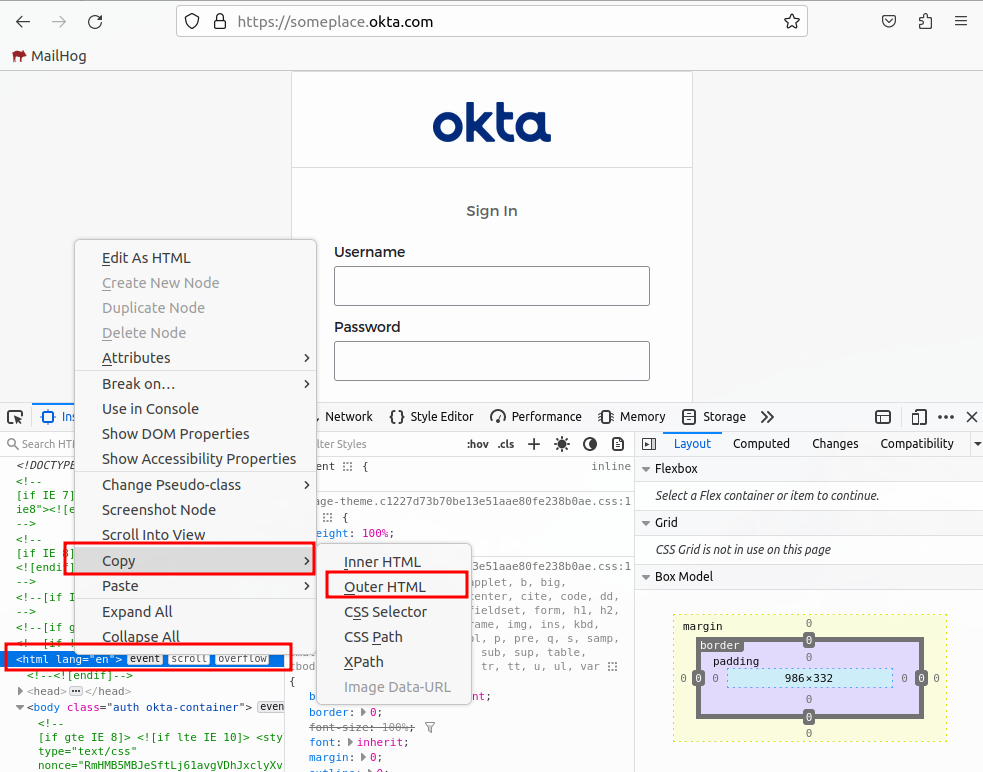
- right click web page > inspect element.
- find top HTML tag.
- right click > copy > outer HTML.
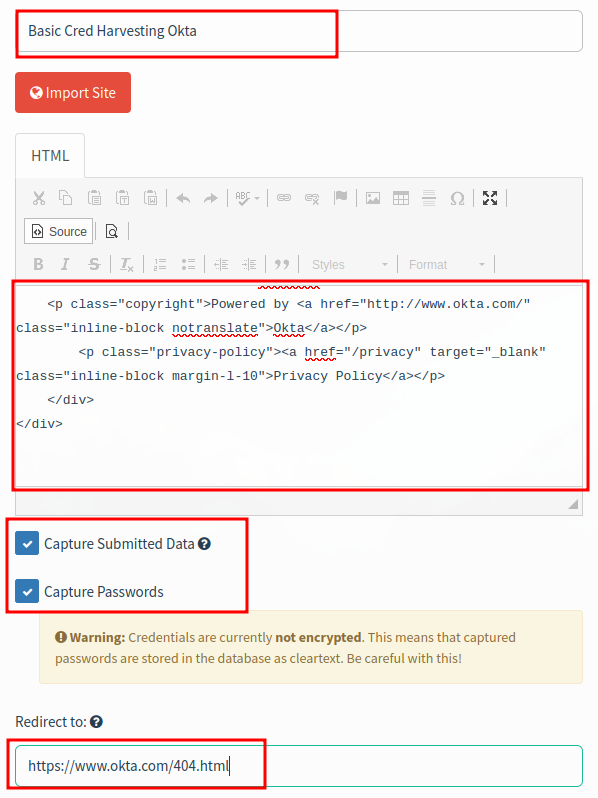
- paste HTML in landing page.
- check capture data.
- check capture password.
- set redirect to https://www.okta.com/404.html
Create a new email template
Be sure to include {{.URL}} ref
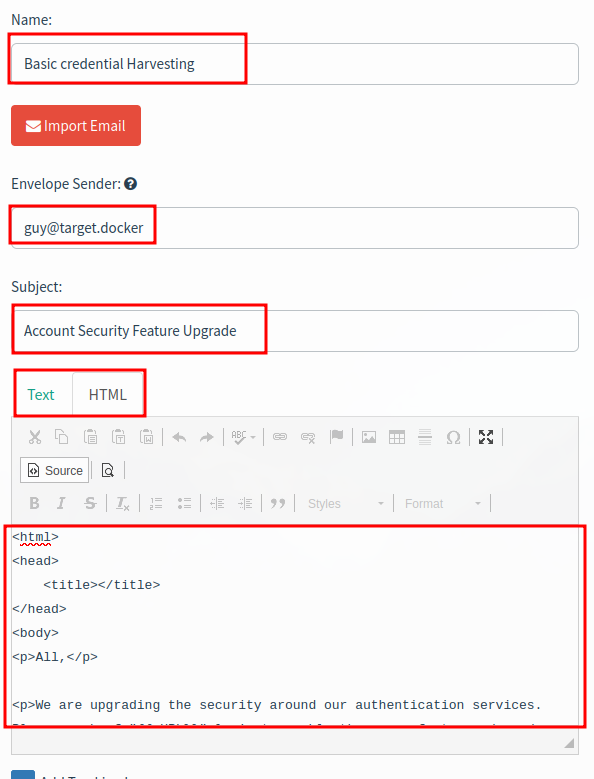
- Name:
Basic credential Harvesting - Envelope Sender:
guy@target.docker - Subject:
Account Security Feature Upgrade
Text:
All,
We are upgrading the security around our authentication services. Please login ({{.URL}}) to enable these new features.
Thanks
-
Guy Withaface
IT
HTML:
<html>
<head>
<title></title>
</head>
<body>
<p>All,</p>
<p>We are upgrading the security around our authentication services. Please <a href="{{.URL}}">login to enable these new features</a>.</p>
<p>Thanks</p>
</body>
</html>
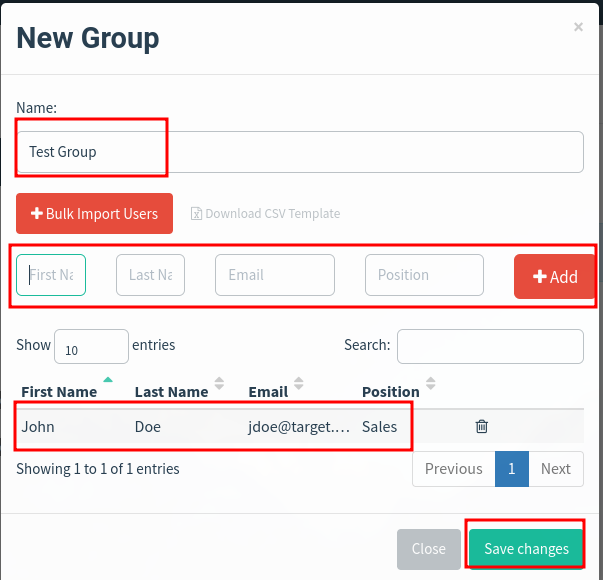
Create a new group to be our target
We can download the CSV template and populate it with our users we found earlier. Then import the CSV template.
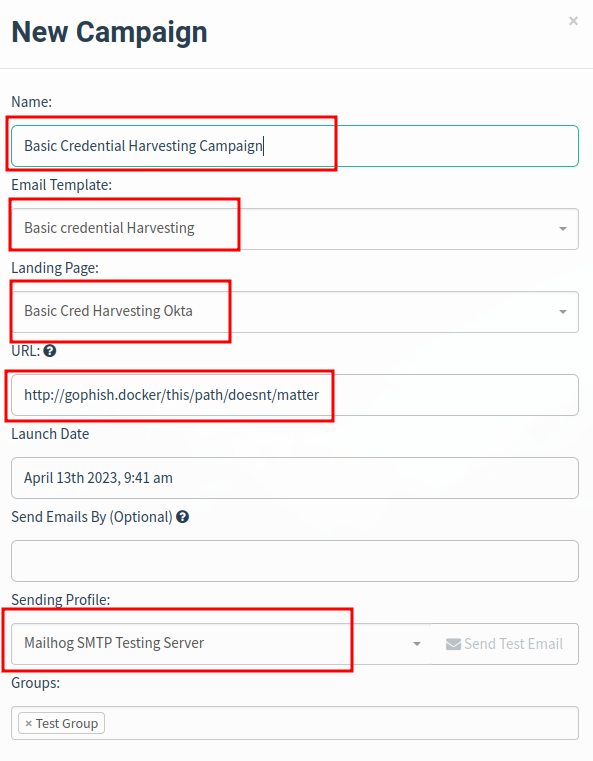
- Create new Campaign that uses the above.
- Use
http://gophish.docker/this/path/doesnt/matterfor the URL.
- Use
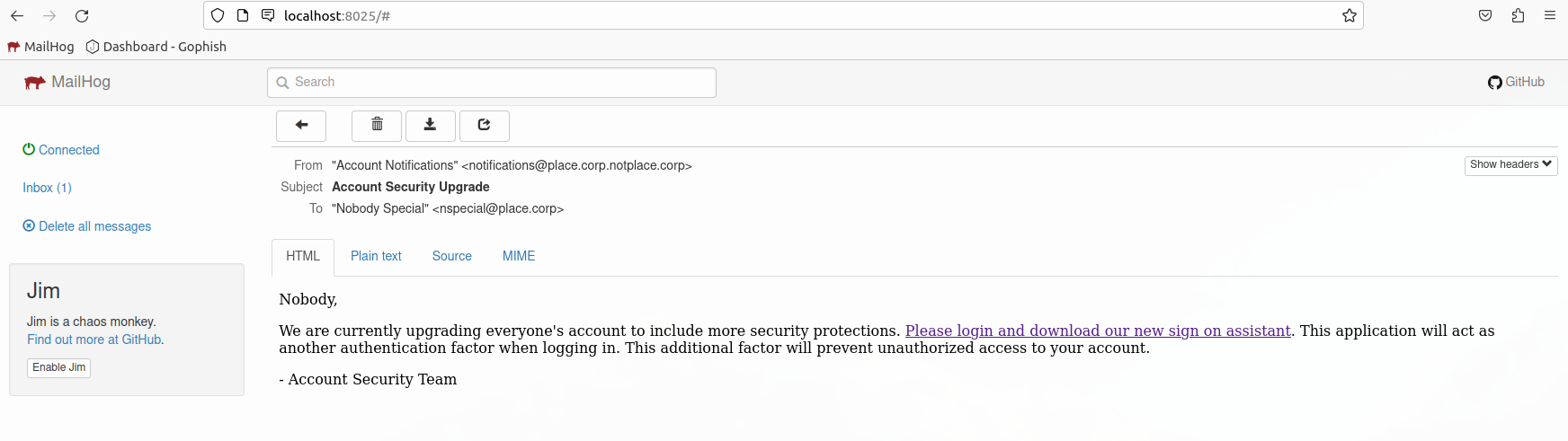
Test email in MailHog
Open MailHog
click link.
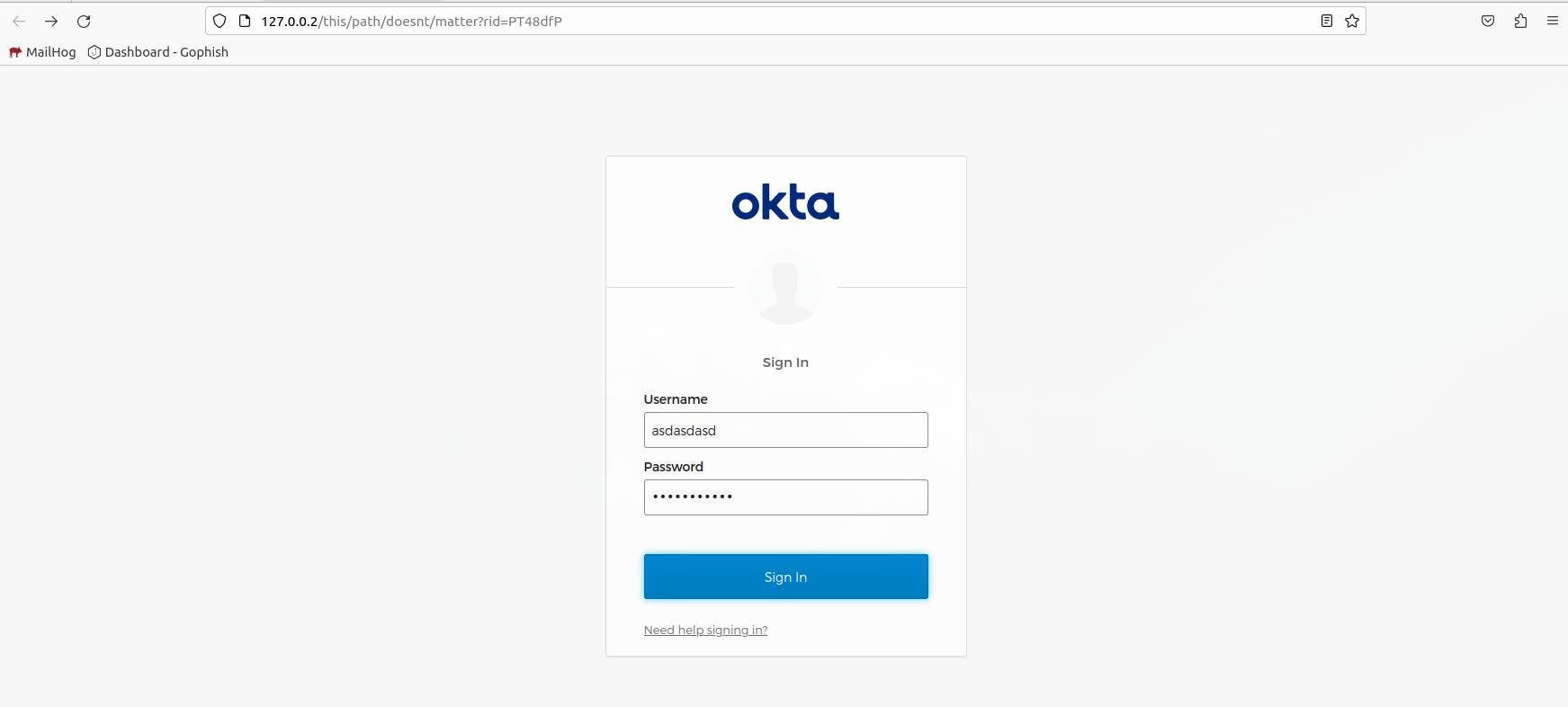
attempt to log in with fake credentials.